Detection of the infection
Fox-IT operates the shared Security Operations Center service ProtACT. This service monitors the networks of our clients for malicious activity. On January 3 we detected and investigated the infection of clients after they visited yahoo.com.
Infection
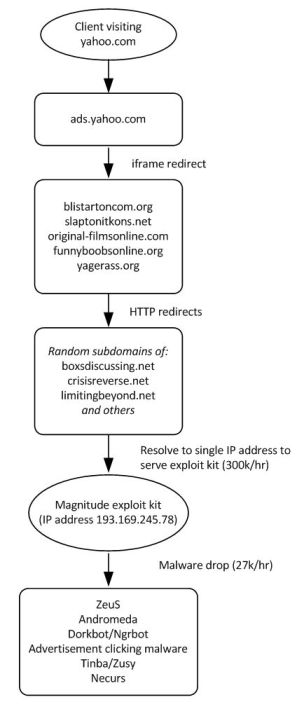
Clients visiting yahoo.com received advertisements served by ads.yahoo.com. Some of the advertisements are malicious. Those malicious advertisements are iframes hosted on the following domains:
- blistartoncom.org (192.133.137.59), registered on 1 Jan 2014
- slaptonitkons.net (192.133.137.100), registered on 1 Jan 2014
- original-filmsonline.com (192.133.137.63)
- funnyboobsonline.org (192.133.137.247)
- yagerass.org (192.133.137.56)
Upon visiting the malicious advertisements users get redirected to a “Magnitude” exploit kit via a HTTP redirect to seemingly random subdomains of:
- boxsdiscussing.net
- crisisreverse.net
- limitingbeyond.net
- and others
All those domains are served from a single IP address: 193.169.245.78. This IP-address appears to be hosted in the Netherlands.
This exploit kit exploits vulnerabilities in Java and installs a host of different malware including:
- ZeuS
- Andromeda
- Dorkbot/Ngrbot
- Advertisement clicking malware
- Tinba/Zusy
- Necurs
The investigation showed that the earliest signs of infection were at December 30, 2013. Other reports suggest it might have started even earlier.
Schematically the exploit looks like this:
Size
Based on a sample of traffic we estimate the number of visits to the malicious site to be around 300k/hr. Given a typical infection rate of 9% this would result in around 27.000 infections every hour. Based on the same sample, the countries most affected by the exploit kit are Romania, Great Britain and France. At this time it’s unclear why those countries are most affected, it is likely due to the configuration of the malicious advertisements on Yahoo.
Motivation
It is unclear which specific group is behind this attack, but the attackers are clearly financially motivated and seem to offer services to other actors. The exploit kit bears similarities to the one used in the brief infection of php.net in October 2013.
Advice
Block access to the following IP-addresses of the malicious advertisement and the exploit kit:
- Block the 192.133.137/24 subnet
- Block the 193.169.245/24 subnet
Also closely inspect network traffic for signs of successful exploits for any of the dropped malware.
Yahoo is aware of the issue and looking into it.
Please watch this page for updates.
Update January 3, 1815 (GMT+1): It appears the traffic to the exploit kit has significantly decreased. It looks like Yahoo is taking steps to fix the problem.

I wonder why those domains are usually dropped after the botnet is taken down. Someone could reregister them while they’re up for grabs…𝌆!
The amount of info we get here is really minimal. Info we should get is stuff like:
– Which versions of Java are affected?
– Which configurations of Java prevent getting affected?
– How do we know if we’re affected?
etc. etc.
p.s.
I read on arstechnica.com (http://arstechnica.com/security/2014/01/malware-attacks-thousands-of-yahoo-com-visitors-through-java-exploit/) that US visitors weren’t affected.
Nice! Another reason to use adblock plus 😉
@MOCaseA
Please explain more about which versions of Java are “old” and which are not, how old is old, how many days / weeks / months / years have passed since an “old” java was updated to a new?
Do you know specifically which versions of java would be old and when a new version came out that it is no longer old?
When was the break from “old” to new, ?
1 year ago? 1 month?, what timeframe are we speaking here
What happens, if the Java-Plugin in Firefox is configured, so the user has to specifically confirm the activation of the Plugin, when needed by the Website. My default settings for Firefox are such, that the Runtime needs manual confirmation, while the Java Deployment Toolkit is completely deactivated.
Is an infaction possible this way?
@Ravi,
The drive-by did not need to be clicked on. The exploitable version of Java allowed the malware to automatically run. Newer versions of Java required the user to click the advertisement.
@JimmyFal,
The older versions of Java allowed the malware to be run automatically. Newer versions required the user to click the ad.
So how can I find out if I’ve been affected by this exploit?
And this is why I use AdBlock Plus.
“it’s unclear why those countries are most affected” – could it be related to the service popularity within those countries? (market share)
Is there more information about:
1. the client operating systems and browsers?
2. the browsers and Java versions affected by the attack?
The reason why people don’t use adblock plugins is beyond me.
This “hosts” configurations will help you so much 😉
http://someonewhocares.org/hosts/
By visiting the page (the ad is displayed on), no actual interaction with the ad is necessary for the infection process to start.
Does the malware affect all version of Java Run Time?
Do you have the stats for “infected platform” and “browser used”?
Isn’t it true, correct me if I am wrong, but you MUST have an outdated version of Java installed on the computer in order for the exploit to take place. Then and only then can you be infected by simply visiting the site. I’m not saying I am 100% correct, but I think I am. So if you remove Java, you cannot be exploited, I believe.
There have been reports in other major online publications that the user had to click on the advert to get infected. Please, send out a formal statement on this to my email if possible. We were among the first ones to cover this story and our readers are demanding a confirmation on this!
“exploits vulnerabilities in Java”. Someone please correct me if I am wrong. Java is hugely exploited on computers. If you have Java on your computer, it must be kept up to date in order to be as protected as possible. However Oracle; the creators of Java see fit to exploit innocent people whom are simply trying to update java regularly, by checking boxes for the end user that routinely change the home page of the browser and install the Ask.com toolbar. A scumbag practice no matter how you slice it. The best way to avoid a java exploit is to go to the control panel on your computer, and REMOVE JAVA. You probably do not need it anyway.
So do we get infected by visiting the page or clicking on the ad?
Thanks, that’s good to know!
My mother still uses this service and I keep trying to get her onto another email service.
Yes, the Yahoo advertisements are blocked by Adblock Plus. A somewhat recent thread on the Adblock forums shows that the filter blocked ads.yahoo as well:
https://adblockplus.org/forum/viewtopic.php?t=18121
Its a drive-by exploit kit, just loading the advertisements was enough to get exploited and infected with malware.
Reblogged this on Southclaw and commented:
I keep trying to convince my mother to stop using Yahoo mail!
Getting malware from simply visiting the site is pretty bad.
Would the use of AdBlock while viewing the site have prevented the malware from being installed?
Upon visiting the malicious advertisements users get redirected to a “Magnitude” exploit kit via a HTTP redirect.. Does this mean that the users will be redirected when they click on the ad or when the ad is displayed? please clarify..